Oracle Internet Directory (OID) Enterprise Scaling, Part 1: Fundamentals & Core Architecture
Table of Contents
ToggleIntroduction
Scaling Oracle Internet Directory (OID) can feel like adding new lanes to a busy highway—an essential step to accommodate growing traffic and ensure smooth performance. In this Part 1 of our OID Scaling Guide, we focus on why scaling matters, the four pillars of successful OID scaling, and the core architecture that underpins your environment.
Navigation:
- You are here: Part 1 – Fundamentals & Core Architecture
- Next: Part 2 – Implementation Strategies & Real-world Applications
Understanding Oracle Internet Directory Scaling
Scaling Oracle Internet Directory (OID) is a complex undertaking that goes beyond simple optimization. If we think of optimization as fine-tuning a car’s engine to maximize its performance, scaling is more akin to adding lanes to a highway to accommodate increased traffic. While optimization focuses on making the most efficient use of existing resources, scaling involves proactively expanding your infrastructure to handle future growth and demand.
Imagine this scenario: your organization is experiencing rapid growth, onboarding hundreds of new users each week. As a result, the volume of authentication requests your OID system must process is skyrocketing. Without a robust scaling strategy in place, your OID environment may start to buckle under this increased load, leading to performance slowdowns and even potential outages. This is where a comprehensive understanding of OID scaling becomes crucial.
**This guide builds on previous optimization techniques, offering a comprehensive approach to ensure your Oracle Internet Directory environment can grow seamlessly with your organization.
Key Concepts:
- Scaling refers to the process of expanding your infrastructure to accommodate increased demand. This might involve adding more servers, increasing CPU or memory capacity, or distributing the workload across multiple systems.
- Optimization, on the other hand, is about tuning and configuring your existing resources to achieve peak performance. This could include adjusting cache sizes, tweaking connection pool settings, or refining your data indexing strategy.
- Effective scaling ensures that your OID system can handle the rapid growth in users and authentication requests that comes with organizational expansion.
- By proactively scaling your infrastructure, you can prevent performance bottlenecks and minimize the risk of system downtime.
- A well-scaled OID environment provides a seamless, responsive user experience even as the demands on the system increase.
Prerequisites for Scaling
Before embarking on your OID scaling journey, it’s important to ensure you have the following prerequisites in place:
- OID version 11g or higher
- A solid understanding of LDAP (Lightweight Directory Access Protocol) and how it works
- Familiarity with Oracle Database concepts and administration
It’s a common misconception that simply adding more servers to your OID environment will automatically solve all performance problems. In reality, truly effective scaling requires a holistic view of your entire OID system, understanding how each component interacts and impacts overall performance.
The Four Pillars of Successful OID Scaling
1. Resource Utilization Analysis
Analyzing resource utilization is like giving your OID system a comprehensive health check-up. You’ll need to closely examine key metrics such as CPU usage, memory consumption, and I/O activity to identify potential bottlenecks or areas of strain. Think of it like managing a factory: by continually monitoring the utilization of your equipment, you can spot overworked machines that may require maintenance, upgrades, or replacement. In the same way, by tracking the resource usage of your OID components, you can pinpoint areas that may become performance bottlenecks as your system scales. Some key resource metrics to monitor include:
- CPU utilization: Are certain processes or components consistently consuming a high percentage of CPU cycles?
- Memory usage: Is your system memory being efficiently allocated and utilized? Are there any memory leaks or areas of excessive consumption?
- I/O activity: Are there any storage or network bottlenecks impacting performance? Are your disks or network interfaces being saturated during peak periods?
By regularly analyzing these resource metrics, you can gain valuable insights into your OID system’s health and identify potential scaling challenges before they impact performance.
2. Growth Pattern Analysis
Just as urban planners must study population growth trends to forecast future infrastructure needs, OID administrators must understand how their system’s workload is evolving over time. This involves analyzing key growth patterns such as:
- User growth rate: How quickly is your organization adding new users? Is this growth linear or exponential? Understanding your user growth trajectory helps you anticipate future authentication request volumes.
- Data volume growth: Is the amount of data stored in your OID directory growing rapidly? Large data sets can impact search and retrieval performance, so it’s crucial to monitor data growth and plan storage scaling accordingly.
- Peak usage times: When does your OID system experience the heaviest loads? Are there predictable usage spikes (e.g., Monday mornings when employees log in for the week)? Identifying peak periods helps you plan for adequate capacity during critical times.
By carefully studying these growth patterns, you can develop proactive scaling strategies to ensure your OID infrastructure stays one step ahead of demand. This might involve gradually adding more servers, increasing storage capacity, or adjusting your load balancing configurations as your organization grows.
3. Performance Metrics Framework
Establishing a robust performance metrics framework is like creating a comprehensive dashboard for your OID system’s vital signs. This involves continuously monitoring key indicators such as:
- Response times: How quickly does your OID system respond to search queries and authentication requests? Slow response times can indicate a need for scaling.
- Throughput: How many operations (e.g., searches, authentications) can your system process per second? If throughput starts to degrade, it may be time to scale up.
- Resource utilization: As discussed earlier, keeping a close eye on CPU, memory, and I/O utilization helps you identify when components are reaching their capacity limits.
- Connection pool utilization: Are your LDAP connection pools efficiently utilized, or are they frequently maxed out? Insufficient connection pooling can lead to performance bottlenecks.
Think of your performance metrics like a patient monitoring system in a hospital. By continuously tracking these vital signs, you can quickly spot potential issues and take corrective action before they escalate into critical problems. Some key tools and techniques for monitoring OID performance include:
- Oracle Enterprise Manager: A comprehensive management platform that provides real-time performance monitoring, diagnostics, and alerting for your OID environment.
- LDAP server logs: Analyzing your LDAP server logs can provide valuable insights into performance issues, error patterns, and usage trends.
- Synthetic transactions: Periodically running simulated user transactions (e.g., authentication requests) can help you proactively identify performance degradation before it impacts real users.
By establishing a robust performance metrics framework and regularly reviewing these key indicators, you can maintain a clear picture of your OID system’s health and scalability over time.
4. Infrastructure Planning
Armed with insights from your resource utilization analysis, growth pattern studies, and performance metrics, you can develop an informed, data-driven infrastructure plan for scaling your OID environment. This involves considering strategies such as:
- Vertical scaling: Also known as “scaling up,” this involves upgrading your existing OID servers with more powerful hardware, such as adding CPUs, increasing memory, or using faster storage devices. Vertical scaling allows you to handle increased workload without adding more servers to your environment.
- Horizontal scaling: Also known as “scaling out,” this involves adding more OID servers to your environment to distribute the workload. By spreading the load across multiple servers, you can improve performance and handle higher concurrency. Load balancers are often used to evenly distribute traffic among the servers.
- Balanced resource allocation: As you scale your OID infrastructure, it’s important to ensure that each component has the resources it needs to perform optimally. This might involve allocating more memory to your OID server processes, increasing the size of your database connection pools, or adjusting your thread pool configurations.
- Caching and indexing optimizations: Implementing effective caching strategies and optimizing your data indexing can significantly improve OID performance as you scale. This might include using server-side caching to reduce the load on your backend systems or fine-tuning your index configurations to speed up search operations.
Some key considerations when planning your OID infrastructure include:
- Capacity planning: Based on your growth projections, how much additional capacity will you need in terms of CPU, memory, storage, and network bandwidth? It’s important to plan for peak usage periods and include some buffer for unexpected spikes.
- High availability: As your organization becomes increasingly reliant on your OID system, ensuring high availability becomes crucial. This might involve implementing failover clusters, load balancing, or data replication to minimize the impact of hardware or software failures.
- Monitoring and alerting: Your infrastructure plan should include robust monitoring and alerting mechanisms to proactively identify and address potential issues before they impact performance. This might include setting up performance thresholds, configuring automated alerts, and establishing incident response protocols.
- Scalability testing: Before deploying any major infrastructure changes, it’s important to thoroughly test your scaling strategies to ensure they deliver the expected performance improvements. This might involve conducting load testing, simulating peak usage scenarios, and measuring key performance indicators.
By carefully planning your OID infrastructure with scalability, performance, and reliability in mind, you can create a solid foundation for your organization’s growth and evolving authentication needs.
OID Architecture Deep Dive
To effectively scale your OID environment, it’s essential to have a deep understanding of its underlying architecture and how each component interacts. The OID architecture consists of four main layers, each with its own specific responsibilities and scaling considerations.
OID System Core Components
This architecture diagram illustrates the key components of an OID system and their interactions. It shows how requests flow from the client layer through WebLogic Server to LDAP services, and ultimately interact with the database layer. Each layer has distinct responsibilities, and proper scaling requires maintaining balance across all of them. Think of it as a blueprint showing how a well-designed OID system orchestrates its various components to handle directory services efficiently.
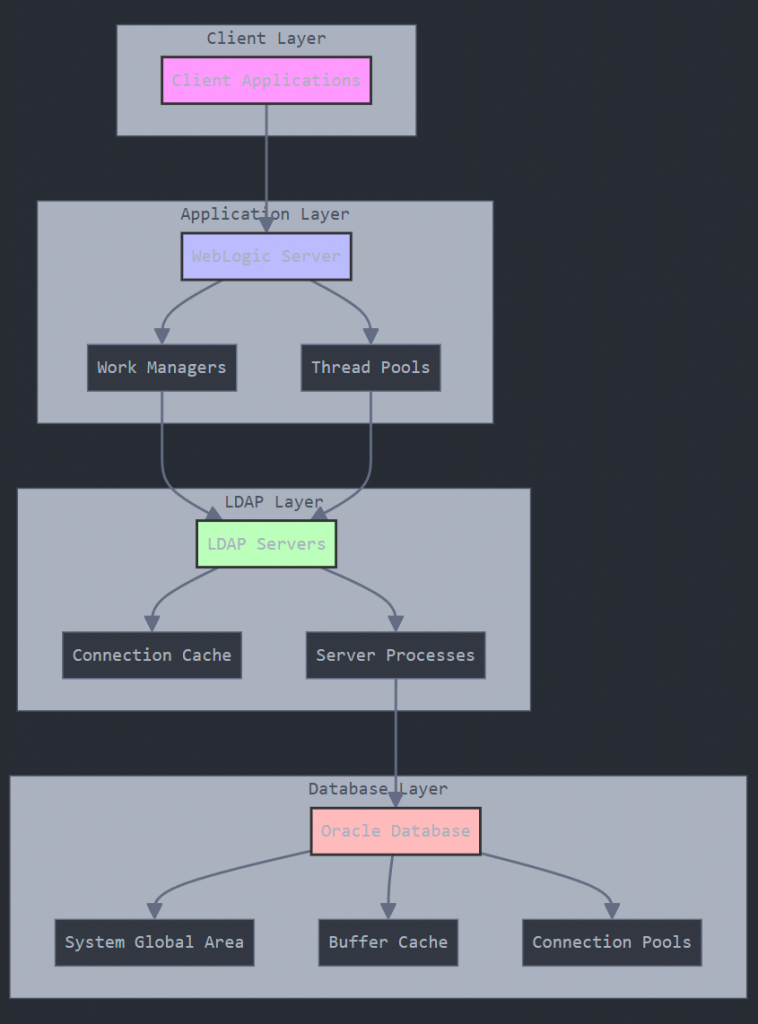
Client Layer: The Entry Point
The Client Layer is the entry point for all interactions with your OID system. It’s like the front desk of a busy office building, handling all incoming requests and directing them to the appropriate resources. Key responsibilities of the Client Layer include:
- Authenticating users and handling login requests
- Processing search queries and update operations
- Enforcing security policies and access controls
As your user base grows, the Client Layer must be able to efficiently handle an increasing volume of concurrent requests. Scaling strategies for the Client Layer might include using load balancers to distribute traffic across multiple OID servers or implementing client-side connection pooling to reduce the overhead of establishing new connections.
Application Layer (WebLogic)
If the Client Layer is the front desk, the Application Layer is the team of workers behind the scenes, responsible for processing and fulfilling client requests. In the OID architecture, the Application Layer is typically implemented using Oracle WebLogic Server. Key components of the Application Layer include:
- Work Managers: These are like the supervisors of the Application Layer, responsible for prioritizing and assigning incoming tasks to the appropriate processing resources.
- Thread Pools: These are the groups of workers that actually carry out the assigned tasks. Each thread pool is optimized for handling specific types of operations, such as authentication requests or search queries.
As your OID system scales, the Application Layer must be able to efficiently manage a growing number of concurrent tasks. Scaling strategies for the Application Layer might include adjusting your thread pool configurations to handle more concurrent operations, implementing advanced work management policies to prioritize critical tasks, or clustering multiple WebLogic servers to distribute the processing load.
LDAP Layer (Core Services)
The LDAP Layer is the heart of your OID system, responsible for handling all LDAP-related operations and managing the directory data. It’s like the central filing room of your office, where all important records are stored and retrieved. Key components of the LDAP Layer include:
- LDAP Server Processes: These are the individual worker processes that handle LDAP operations, such as search, add, modify, and delete requests.
- Connection Pools: These manage the connections between the LDAP server processes and the underlying database, allowing for efficient reuse of database connections.
As your OID system grows, the LDAP Layer must be able to efficiently process an increasing volume of LDAP operations while maintaining data consistency and integrity. Scaling strategies for the LDAP Layer might include increasing the number of LDAP server processes to handle more concurrent operations, tuning your connection pool settings to maximize database efficiency, or implementing data partitioning to distribute the directory data across multiple storage devices.
Database Layer (The Foundation)
The Database Layer is the foundation of your OID system, responsible for securely storing and managing all the directory data. If the LDAP Layer is the filing room, the Database Layer is the actual file cabinets where the records are kept.
In a typical OID deployment, the Database Layer is implemented using Oracle Database, which provides a scalable, high-performance, and highly available data storage solution.
Key considerations for scaling the Database Layer include:
- Data storage capacity: As your directory data grows, you must ensure that your database has sufficient storage capacity to accommodate the increased data volume. This might involve adding more disk drives, implementing data compression, or using advanced storage technologies like Oracle Automatic Storage Management (ASM).
- Database performance: To maintain optimal OID performance, your database must be able to quickly process a high volume of read and write operations. This might involve tuning your database parameters, optimizing your data indexing strategies, or using advanced performance features like Oracle Real Application Clusters (RAC).
- Backup and recovery: As your directory data becomes increasingly critical to your organization, ensuring reliable backup and recovery processes becomes essential. This might involve implementing regular data backups, using Oracle Data Guard for real-time data replication, or creating a comprehensive disaster recovery plan.
By carefully designing and scaling your Database Layer to meet the needs of your growing OID system, you can create a solid foundation for reliable, high-performance directory services.
Component Interactions and Performance Impact
Understanding the interactions between these architectural layers is crucial for effective OID scaling. Each layer must be carefully tuned and optimized to work in harmony with the others, like a well-choreographed dance.
For example, if you increase the number of thread pools in your Application Layer to handle more concurrent requests, but your Database Layer is undersized and cannot keep up with the increased query volume, you may actually degrade overall system performance. Similarly, if you scale up your LDAP Layer by adding more server processes, but your Client Layer is not optimized for efficient connection management, you may experience high latency and poor response times.
Effective OID scaling requires a holistic approach that considers the interdependencies and performance characteristics of each architectural layer. By carefully analyzing your resource utilization patterns, studying your system’s growth trends, establishing a robust performance monitoring framework, and developing a comprehensive infrastructure plan, you can create an OID environment that scales seamlessly with your organization’s evolving needs.
Performance Metrics Framework
Establishing a robust performance metrics framework is like creating a comprehensive dashboard for your OID system’s vital signs. This involves continuously monitoring key indicators such as:
- Response times: How quickly does your OID system respond to search queries and authentication requests? Slow response times can indicate a need for scaling.
- Throughput: How many operations (e.g., searches, authentications) can your system process per second? If throughput starts to degrade, it may be time to scale up.
- Resource utilization: As discussed earlier, keeping a close eye on CPU, memory, and I/O utilization helps you identify when components are reaching their capacity limits.
- Connection pool utilization: Are your LDAP connection pools efficiently utilized, or are they frequently maxed out? Insufficient connection pooling can lead to performance bottlenecks.
Think of your performance metrics like a patient monitoring system in a hospital. By continuously tracking these vital signs, you can quickly spot potential issues and take corrective action before they escalate into critical problems. Some key tools and techniques for monitoring OID performance include:
- Oracle Enterprise Manager: A comprehensive management platform that provides real-time performance monitoring, diagnostics, and alerting for your OID environment.
- LDAP server logs: Analyzing your LDAP server logs can provide valuable insights into performance issues, error patterns, and usage trends.
# Connection monitoring command
ldapsearch -h -p -D cn=orcladmin -w -b \
"cn=client connections,cn=monitor" "(objectclass=*)"
- Synthetic transactions: Periodically running simulated user transactions (e.g., authentication requests) can help you proactively identify performance degradation before it impacts real users.
Key Performance Indicators
Understanding your system’s vital signs requires monitoring three critical areas:
1. Memory Health Metrics
Memory health in OID systems is like managing the workspace in a busy office. Just as an overcrowded office reduces productivity, insufficient memory can severely impact system performance:
- Available Memory: When free memory drops below 15%, systems require immediate attention, much like an overcrowded workspace that needs immediate reorganization
- Swap Usage: Exceeding 5% swap usage indicates potential performance issues, similar to when an office must constantly move materials between storage and workspace
- Page Faults: Increasing page fault rates suggest growing memory pressure, like workers constantly searching for misplaced documents
2. CPU Performance Metrics
CPU usage patterns are like monitoring the workload of your processing team:
- Sustained Usage: CPU utilization above 70% warrants investigation, like a team consistently working at maximum capacity
- Critical Threshold: Usage exceeding 85% signals immediate scaling needs
- Load Distribution: Per-core load above 0.7 indicates potential processing bottlenecks
3. Connection Health Metrics
Connection management is similar to managing customer service channels in a busy organization:
- Session Utilization: Usage above 75% suggests preparing for scaling, like seeing your service channels getting consistently busy
- Wait Times: Extended wait periods indicate needed connection pool adjustments
- Timeout Patterns: Recurring timeouts reveal underlying capacity constraints
By establishing a robust performance metrics framework and regularly reviewing these key indicators, you can maintain a clear picture of your OID system’s health and scalability over time.
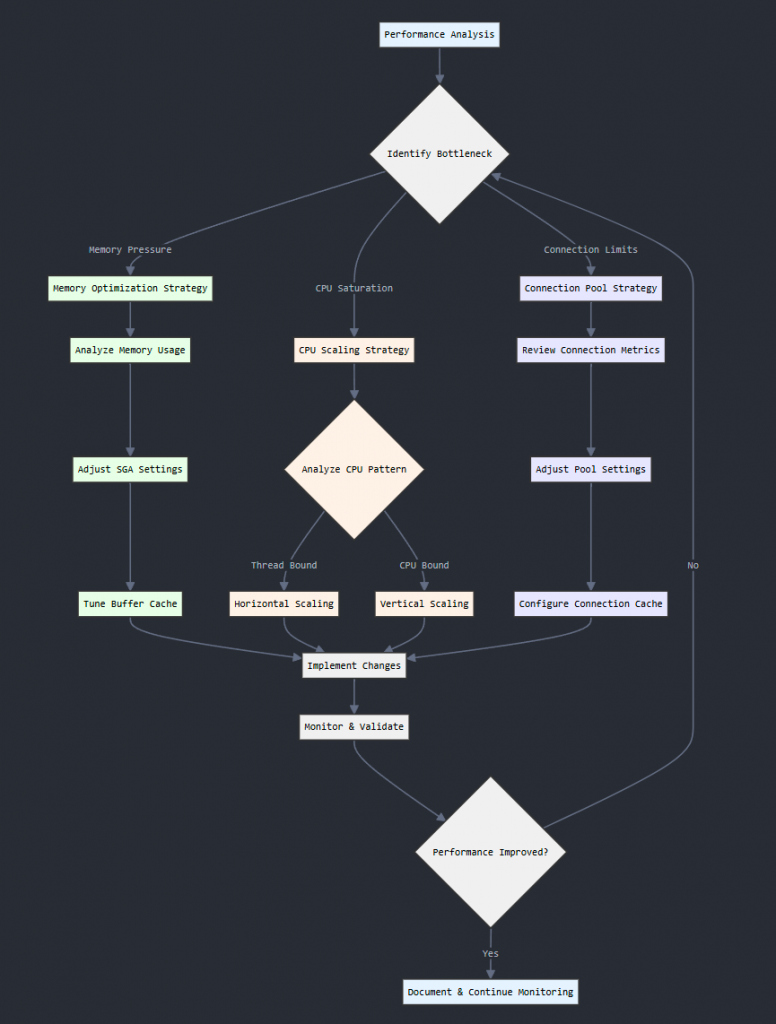
Decision Making Process
Making scaling decisions follows a systematic approach, much like medical diagnosis and treatment:
1. Analysis Phase
This phase is about gathering comprehensive data about your OID system’s current state and performance, similar to a doctor taking a patient’s history and conducting initial exams. Key activities in this phase include:
- Collecting performance metrics across all components (CPU usage, memory utilization, I/O activity, etc.)
- Establishing baseline performance levels to help identify anomalies
- Identifying any deviations from expected behavior or performance
The goal is to create a detailed snapshot of your system’s health that will guide further investigation and diagnosis.
2. Diagnosis Phase
With the data collected in the Analysis Phase, the next step is to pinpoint the root causes of any identified performance issues, similar to a doctor interpreting test results to diagnose an illness. This involves:
- Analyzing performance metrics to identify bottlenecks or resource constraints
- Tracing issues back to specific components or layers (e.g., Database, LDAP, Application)
- Assessing the impact of identified issues on overall system performance and user experience
The outcome of this phase should be a clear understanding of the specific factors limiting your OID system’s scalability and performance.
3. Solution Selection
Once the root causes of performance issues have been diagnosed, the next phase is to develop a targeted treatment plan. This involves:
- Evaluating different scaling approaches (vertical scaling, horizontal scaling, etc.) based on the diagnosed issues
- Assessing the potential impact and trade-offs of each approach (cost, complexity, time to implement, etc.)
- Selecting the scaling strategy that best addresses the identified issues while aligning with business goals and constraints
The key is to choose a solution that not only resolves the immediate performance problems but also sets the stage for long-term scalability and growth.
4. Implementation and Validation
The final phase is to put the selected scaling solution into action and verify that it delivers the expected results, much like a doctor monitoring a patient’s response to treatment. This involves:
- Carefully planning and executing the implementation to minimize risk and disruption
- Continuously monitoring system performance and key metrics to track the impact of the changes
- Comparing pre- and post-implementation metrics to quantify the improvement in performance and scalability
- Making any necessary adjustments or optimizations based on the observed results
The goal of this phase is to ensure that the selected scaling approach effectively resolves the identified performance issues and delivers a measurable improvement in system health and user experience.
By following this structured decision-making process, you can approach OID scaling in a methodical, data-driven way that maximizes the chances of success while minimizing risk and disruption. It provides a framework for continuously monitoring, diagnosing, and optimizing your OID system to ensure it stays healthy and responsive as your organization grows and evolves.
In the next section, we’ll explore how to implement these concepts in real-world scenarios, turning this theoretical framework into practical solutions for your OID infrastructure.
Conclusion of Part 1
By mastering these fundamentals—the four pillars, OID architecture insights, and a metrics-driven decision process—you’re ready to begin practical implementations. In Part 2, we’ll dive into memory optimization, connection management, and real-world use cases to bring these concepts to life.
Stay tuned for Part 2: Implementation Strategies and Real-world Applications.






3 Comments